Yes this wpad automatic proxy solution was used by our previous server, and also by Linuxschools.
Yes, we are happy that the server is finally working ![]() , but I’m not sure which direction to take, but then I think it’s worth reading more about Linbo, if I understand correctly, there are hardware classes that have to be created on a virtual machine first, and then they have to be loaded back to the client with pxe? On the previous server, I took a picture of a real client that was installed and fully configured, then cloned it back to clients with similar deployments.
, but I’m not sure which direction to take, but then I think it’s worth reading more about Linbo, if I understand correctly, there are hardware classes that have to be created on a virtual machine first, and then they have to be loaded back to the client with pxe? On the previous server, I took a picture of a real client that was installed and fully configured, then cloned it back to clients with similar deployments.
Let’s say the typical clients are Win 10 and 11, or Win 10/11 and Linux with multiboots, is it possible to make such a virtual image with Linbo? And there are also some with a smaller ssd and a bigger hdd and the former only has the systems and the latter the users folders.
There are a lot of questions, I guess I will have to learn more about the system. ![]()
Let’s say the snapshots of Proxmox will help me if something goes wrong, but as I see it handles snapshots incrementally by default, I wonder if it is possible to set fixed backups, which can be reverted to at any time without breaking down the increments.
Yes – that’s one possible way. LINBO is one of the best core features of your new server and it’s a great way to keep every client clean from malware and let them repair by PXE-magic whenever it’s necessary.
We use a VM as master-client (but generally any client can be a master-client); one for Ubuntu-Clients and one for Win10. Whenever there’s a change (new software or anything else) it’s quite easy to start the VM on Proxmox, make all changes and upload a new full image to the server. There’s running a torrent-daemon on the linuxmuster-server. So the clients are seeders when they start via PXE. To get an impression of LINBO, I have attached an old photo. These monitors were changed meanwhile.
Multiboot is possible too as you can see in my picture. So far we don’t use Win11 but there’s a (not so long) thread about it in this forum.
And yes: you can setup some hardware classes (different hardware, non-compatible setups…) whenever it’s necessary. On Linux-clients we don’t need different images here as it runs on any client without problems. Windows is sometimes a bit more problematic but no need to panic.
You don’t need the proxmox snapshots for LINBO. Whenever an uploaded image doesn’t run on a second client you can simply upload a new one to the lmn-server and see if it works better. Depending on the software installed, the image can quickly become relatively large but nevertheless it works like a charm.
And:
See #193
![]() … time to start a new thread …
… time to start a new thread … ![]()
Your problem is fixed
Cool, then no one else will run into this bug.
So either a physical or vm client can be the master client (but indeed the latter seems a more reasonable choice, only then it has to take up some space on the proxmox), but the point is to create that first, from which the initial image is created, which I can then clone with pxe to another client if needed.
Yes I know that the Linux kernel comes with the drivers by default, so you don’t need different images and with newer Windows it’s not that much of a problem anymore, unless the motherboard chipset/generation is very different.
But for the time being, far from it, there is no need and no time to re-clone every client, so automatic proxy distribution will still be an issue, either with wpad or gpo, but I will put that in a separate topic from tomorrow when I can deal with it in a more meaningful way on the test system.
And yes, having both linbo and exam mode at the same time and an active forum was the reason I finally decided to use Linuxmuster ![]() , Sambaedu has a very good cloning module and Veyon is easy to integrate, but there is no exam mode, only French language available (the recommended eole amon firewall and proxy are also) and the forum is closed, only a mailing list. Linuxschools has an exam mode and a slightly more user-friendly proxy, but no really good cloning module and a less spinning forum, but I found all three distros usable and was glad to have a choice.
, Sambaedu has a very good cloning module and Veyon is easy to integrate, but there is no exam mode, only French language available (the recommended eole amon firewall and proxy are also) and the forum is closed, only a mailing list. Linuxschools has an exam mode and a slightly more user-friendly proxy, but no really good cloning module and a less spinning forum, but I found all three distros usable and was glad to have a choice.
And my Proxmox question was more about the server, that snapshots are incremental, but it would be nice to have some fixed backups, but I guess that’s what backup (pbs) is for.
And my dns question, will it be a problem if I open so many new topics? ![]() Such a general starter topic would be fine, or even if there is faq.
Such a general starter topic would be fine, or even if there is faq.
No problem. Just create a VM, enter its (virtual) Proxmox-MAC-address into devices.csv and register it with linuxmuster-import-devices as if it was a bare-metal installation. Then you can boot this VM via PXE as well and handle it like any other client. Of course, you can also use a „real client“ once to first create a LINBO-image and then copy it to the virtual. After this step you can use the virtual client as the new master-client. The only tricky part is to use a good partition table that LINBO can use for all clients afterwards.
No, that’s not a problem. Just do it and we’ll see who responds.
Proxmox is able to create full backups or snapshots – just the way you want it.
But with a PBS on top things are very easy …
![]() a good choice
a good choice ![]() … you can try to translate this play on words into Hungarian:
… you can try to translate this play on words into Hungarian:
linuxmuster.net(t)
Ok, I might flood the forum a bit from tomorrow. ![]()
The Hungarian mirror translation of linuxmuster is Minta Linux, not bad, but it doesn’t really indicate that it’s a school system, Példa Linux is more like it, but it doesn’t really sound Hungarian, so the right translation would need to be thought about to match the logic and sound of the Hungarian language. In Hungarian there are a lot of adjectives (most of our words are) and synonyms to express nuances, so there are alternatives, just a good idea or suggestion is needed, it’s a bit of a literary translation task to translate something into Hungarian, so that it sounds good in Hungarian.
![]() it’s much easier than you thought:
it’s much easier than you thought:
.net is just the suffix but
„nett“ is the german word for „nice | kind | pleasant“
(it is the motto in this forum)
Unfortunately, I don’t understand much German, so I’m sure I won’t understand such linguistic subtleties and puns by default, but now I understand what you mean. ![]()
Hi Fenyo,
i want to add some INformation to yours.
You wrote:
thats not correct.
The server is creating a pair of ssl keys on install and it signes them by itselfe. So there you have a selfsignes pyir of keys which will be seen as „not secure“ by any browser. The certification Authority of the keys is not in your browser. You cloud import it, then the „crossed out“ would be gone: changing nothing on the keypair itselve.
Long story short: the crossed out ssl in Browser is normal and to be expected and has nothing to do with the security of the setup.
To me this is no indicator that the setup did not run through correctly.
Yours
Holger
Hi Fenyo,
again i want to point out a potential „wrong idea“ on your side.
You said:
this way its not true.
The true Statement is:
„and it shouldn’t be for a domain USER“
So there there should be no question about authentication if:
- the Proxy is set correktly
- and you are logged in with a domainuser that is NOT global-admin
global-admin is not working at this point since he is not part of the AD-branch „default-school“: he is in the Brnach ADMINISTRATION.
I know this seems quite wrong, but in a big setup with multiple schools on one server, he cant be „in“ one school, he has to be „above“.
Yours
Holger
Hi Fenyo,
did you see, that Thomas fixed the Issue that kept you so long from a sucsessfull setup?
I thank you very much for your perseverance on this Problem.
You found a BUG and kept working on it until we had a chance to find and fix it.
I appreciate your patiance.
yours
Holger
Hi Holger,
Okay, thanks for the additions, I’ve learned something again. So, for self-signed ssl keys, it is normal to have crossed out https. What else is normal, I can only reach webui from ip address, but not from hostname?
Yes to proxys question, meanwhile I also found out that it doesn’t work with global-admin, now I know exactly why, it works with normal domain user, but for now only if I manually set the global proxy settings, it doesn’t work automatically, but I opened a separate thread for that.
And the DNS problem for some elte domain-ending websites could be easily solved with unbounded dns override, as I found the solution for quota problem in an earlier thread. I’ll have to dig into Linbo more, but for now I don’t know where to start, and I’ve read the Thomas bug fix. ![]()
Once I had the same question … it’s in german but you’ll understand it with a translator:
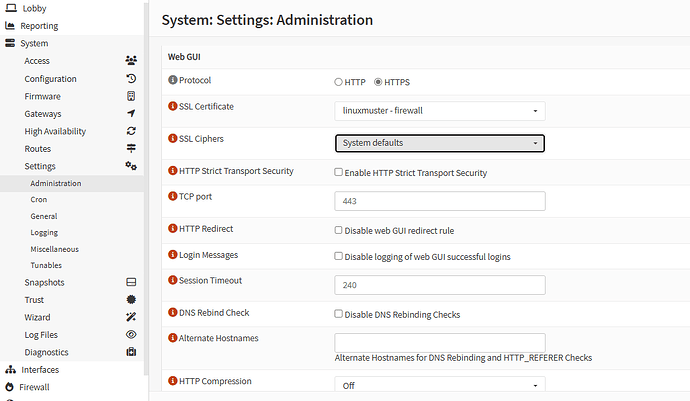
And check on your OPNSense → System → Einstellungen → Verwaltung
Here you can set the cert and the port for the OPNSense UI.
Without further background, I wouldn’t claim to fully understand what the above post is about, in the opnsense settings mentioned above, linuxmuster - firewall is specified as ssl authenticator, I guess that’s fine. What might be an issue later on, if someone wants to access their homes or groupes folders remotely, is there some service (some kind of cloud) or webui itself for that, although I guess that’s not recommended.
You need to install edulution.io on top for this feature … it’s a smart way to let all students access their /home-directory (later).
Another way is: Nextcloud and mount the /home-Dir as a cifs-Share.
Thank you, I will look into that when the time comes. ![]()
To tell a long story short:
When you use an official cert you won’t get a warning that your browser doesn’t trust it because the CA that built the client-cert is known and trusted. You can find a list of all trusted CAs in /etc/ssl/certs. When your browser comes along with a self-signed cert you will get a cert-warning as the (self-created) CA is not part of the list in /etc/ssl/certs. Of course you can copy your own ca-certs to this folder but you’ll have to do it on every client that wants to open the site.
So at the end of the day it’s easier to use a Let’s Encrypt Cert … the CA-certs can be found in the folder with the name ISRG_Root. On Ubuntu-Clients the list can be updated with update-ca-certificates but this is done automatically whenever there are system-updates of the debian/ubuntu-package ca-certificates
You can test the chain of trust with
openssl s_client -connect foo.whatever.com:443 -CApath /etc/ssl/certs
in this case the command uses the given CApath and searches there for the CA-cert.